Infrastructure as Code for Fintech
If you build fintech products, you live in a constant state of tension. On one side, you need startup speed: new features, new markets, new partners. On the other hand, you operate in an environment where a misconfigured security group or an undocumented database can turn into a regulatory incident, not just a bad deploy.
This is exactly the space where Infrastructure as Code (IaC) earns its keep. Instead of infrastructure living in consoles, wikis, and the heads of a few senior engineers, it becomes code: versioned, reviewed, and executed by automation. For fintech teams, that combination of speed and control is hard to achieve any other way.
In what follows, we’ll look at why fintech infrastructure is uniquely demanding, what IaC looks like in practice, how it supports compliance and security, and where tools such as Terraform, OpenTofu fit into the picture.
Why Fintech Infrastructure is a Different Beast
Most SaaS companies care about uptime, latency, and cost. Fintech must also consider the needs of regulators, auditors, card schemes, and banking partners. You handle money flows and sensitive data, making you both an attractive target for attackers and a focal point for compliance.
Typical additional constraints include:
- Heavy regulation: PCI DSS, PSD2, SOC 2, ISO 27001, local banking and data-residency rules, often across multiple regions.
- High data sensitivity: payment data, PII, transaction histories, fraud signals.
- Complex integrations: card processors, banks, KYC/AML providers, credit bureaus, payment networks.
Early on, it’s common to bootstrap infrastructure directly in the cloud console. That works while you are trying to get a prototype into customers’ hands. The trouble begins when you add more environments, expand to new regions, or prepare for your first serious audit. Someone asks how production was built, and the best you can offer is a rough diagram and a lot of hand-waving. Another person asks who loosened a particular firewall rule, and you realise there’s no reliable change history.
These are classic symptoms of manual, organically grown infrastructure. In a typical SaaS company, they are a nuisance. In fintech, they turn into risk.
What Infrastructure as Code Actually Means
Infrastructure as Code is a simple idea with big consequences:
You describe your infrastructure in code, store that code in version control, and let automated systems apply it.
In concrete terms, that usually means:
- A declarative IaC tool such as Terraform or OpenTofu to define cloud resources (networks, databases, queues, IAM policies, and so on).
- Configuration management like Ansible or cloud-init for OS-level setup and operational tasks.
- Kubernetes manifests or Helm charts for the application-runtime layer.
- CI/CD or an IaC platform to run plans, validations, policy checks, and applies in a controlled environment.
When an engineer wants to change infrastructure, they open a pull request instead of logging into the console. CI or an IaC orchestrator generates a plan, shows what will change, applies policy checks, and once the change is approved, applies it using locked-down credentials.
The result is that infrastructure changes resemble code changes: they are reviewable, testable, auditable, and repeatable.
Why IaC Fits Fintech So Well
Built-in Auditability and Change Management
Regulated organisations are repeatedly asked the same questions:
- Who changed production?
- What exactly did they change?
- When did they do it?
- Why was that change approved?
With IaC, answers to those questions live in:
- Git history and pull requests (who, what, when).
- Pipeline logs (how and when it was applied).
- Linked tickets and change records (why).
You can show an auditor a specific version of your Terraform/OpenTofu code, the corresponding plan, the approvals on the pull request, and the logs from the apply. That is a far stronger story than screenshots and tribal knowledge.
Consistent Environments Instead of Snowflakes
Fintech companies rarely operate in a single environment. You might have development, test, staging, and production environments, plus separate stacks for EU, UK, and US to meet data-residency obligations, and possibly sandboxes for partners.
If each environment is built and patched manually, they drift apart:
- Staging carries a “temporary” firewall tweak that never made it into production.
- One region uses a different encryption setting “just for now”.
- An engineer fixes something in one environment and forgets to replicate the change elsewhere.
With IaC, you define the pattern once and instantiate it multiple times with different parameters. Dev and staging use smaller instance sizes; production uses more replicas; the European region writes to an EU-only store. The structure is the same. That makes it far easier to reason about changes and risk, because you no longer treat every environment as a unique snowflake.
Security Built Into the Design
Security reviews often reveal the same recurring issues: missing encryption, overly broad IAM roles, open storage buckets, or inadequate network isolation. If you fix them manually, you will have to fix them repeatedly. If you fix them in IaC modules, you fix them once, and every future deployment inherits the improvement.
You might create:
- A standard database module that always enables encryption at rest, enforces backups, and restricts network access.
- A standard service module that automatically adds a load balancer with TLS, logging, health checks, and rate limiting.
- A standard VPC pattern with public/private subnets, egress control, and centralised logging.
Additionally, policy as code enables you to encode the rules that must never be broken. Policies run on every plan and can simply reject changes that try to create an unencrypted database, deploy to a forbidden region, or expose a sensitive port. Spacelift’s guide “What Is Policy as Code (PaC) & How Do You Implement It?” is a practical introduction to this way of working.
Speed With Guardrails
Fintech is competitive. You cannot spend weeks waiting for infrastructure tickets to be fulfilled. IaC provides engineers with a self-service model: they propose changes in code, view the impact via a plan, and if checks pass, automatically update their infrastructure.
This also unlocks patterns that are hard to achieve manually:
- Short-lived performance test environments for big releases.
- Temporary stacks for complex partner integrations.
- Quick experiments in new regions while staying within security and compliance constraints.
When you run these workflows through an IaC-focused platform, you layer on role-based access control, secrets management, and drift detection, so speed doesn’t come at the cost of control.
Incident Response and Disaster Recovery
When an incident happens, two questions matter:
- What is the current state of the system?
- How quickly can we get back to a safe state?
With IaC, the code describes your intended state. If an environment is badly misconfigured, you can recreate it from scratch using the same definitions. You can also rehearse disaster recovery: simulate region failures, test failover procedures, and show your auditors that recovery is not just a slide in a presentation, it is an automated process you run regularly.
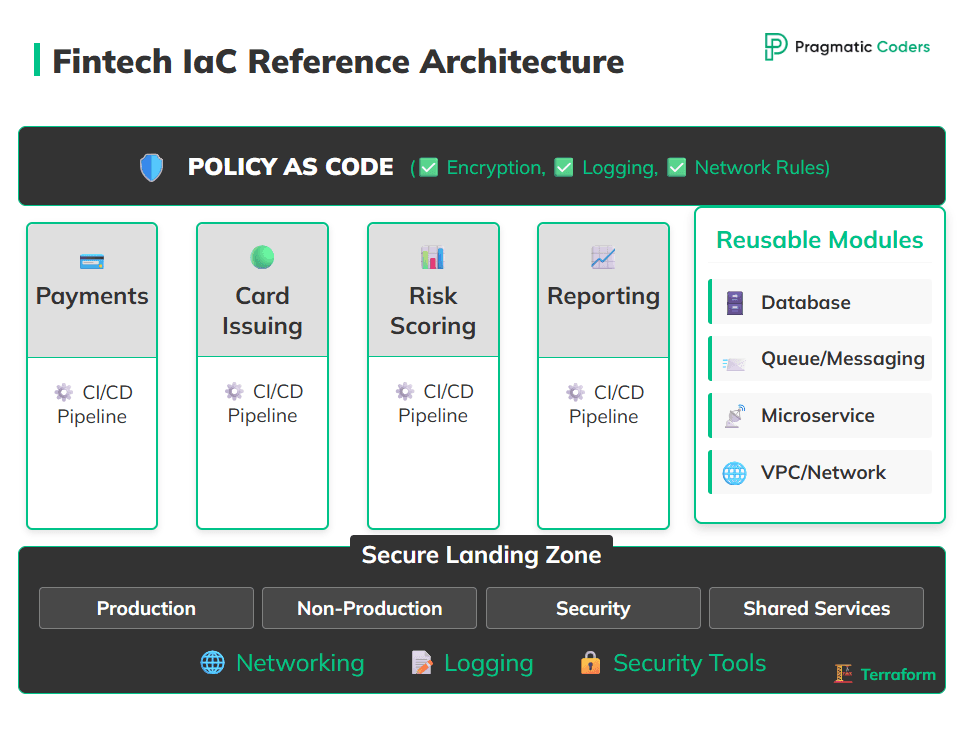
A Reference IaC Architecture for Fintech
There is no single canonical architecture, but many fintech teams converge on a similar structure.
At the base, they create a secure landing zone for each cloud provider and region. That typically includes:
- Accounts or subscriptions split by environment and purpose (prod, non-prod, security, shared services).
- Standardised networking (VPCs, subnets, routing, peering, transit gateways).
- Centralised logging, metrics, and sometimes dedicated security tooling.
This landing zone is itself defined in Terraform or OpenTofu, usually in a separate repository.
Additionally, infrastructure is organized around business domains, not just technical layers. Payment processing, card issuing, risk and scoring, and internal reporting might each get their own IaC configurations and pipelines. Each domain has clear ownership and a bounded blast radius: changes in reporting cannot accidentally break card issuing.
To avoid every team reinventing the wheel, they maintain a library of shared, hardened modules. Teams pull in modules for databases, services, queues, and VPCs that already meet agreed security and compliance standards. Policy as code then enforces the non-negotiable parts of those standards encryption, logging,and network exposure whenever someone tries to deploy a change.
Infrastructure management platforms align naturally with this structure. You define stacks per domain or per environment, attach policies and variables, and get per-stack histories and drift detection. The same high-level approach works with a DIY pipeline too, as long as you are disciplined about ownership and separation.
Terraform, OpenTofu, and Orchestration Platforms
IaC is a practice, not a product; however, you still need to choose tools.
Many teams adopt the HashiCorp Configuration Language ecosystem. That usually means Terraform or OpenTofu:
- Terraform is widely adopted and has a huge ecosystem of modules and examples.
- OpenTofu is a community-driven fork of Terraform with a fully open-source license and a workflow that is very similar to Terraform’s, making it attractive to organisations that are sensitive to vendor lock-in and licensing changes.
You then need something to run your IaC. Some organisations are happy with a general-purpose CI/CD system. Others prefer an IaC-dedicated orchestrators, which wraps Terraform, OpenTofu, and similar tools in workflows that include:
- Centralised secrets and cloud credentials
- Policy-as-code evaluation
- Role-based access control
- Detailed audit logs and drift detection
The right answer depends on your appetite for building internal tooling versus adopting a platform, but in either case, the core IaC principles stay the same.
Embedding Compliance Into the Deployment Pipeline
One of the biggest challenges in fintech is integrating modern engineering practices with traditional change management expectations. Many organisations still expect tickets, approvals, and formally documented control evidence.
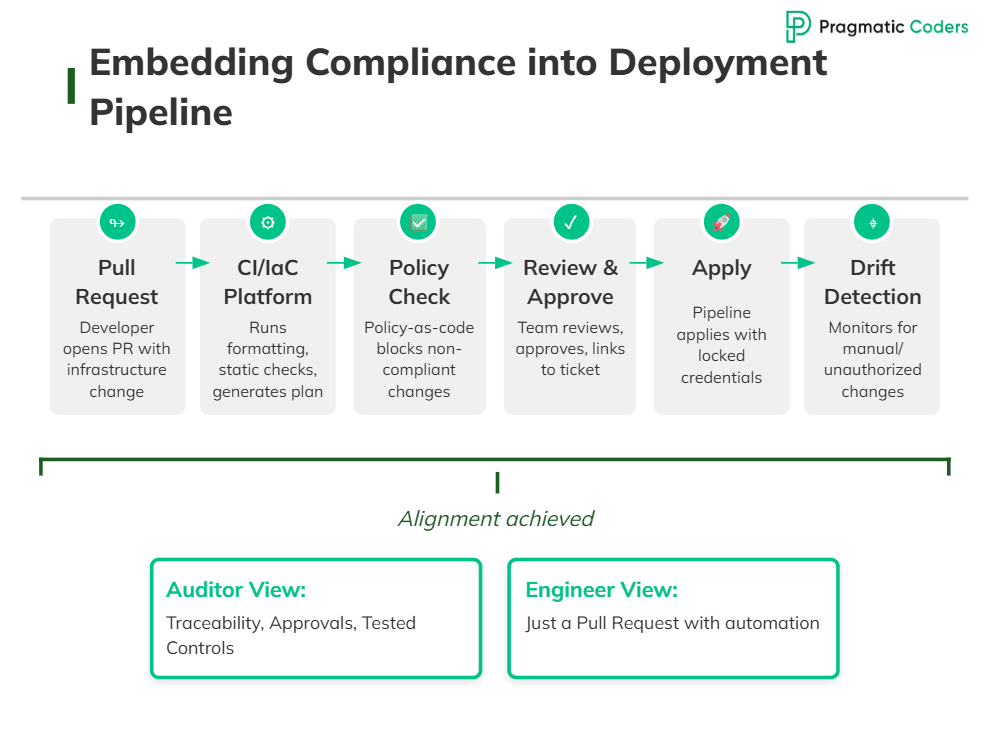
IaC lets you bake those requirements into everyday work, rather than bolting them on afterwards. A typical workflow looks like this:
- A developer opens a pull request with an infrastructure change.
- CI or an IaC platform runs formatting, static checks, and a plan, and posts the result back to the pull request.
- Policy-as-code rules inspect the plan and block any change that violates security or compliance requirements.
- Reviewers from the responsible team (and sometimes security) approve the change, usually linking it to a ticket or change record.
- A controlled pipeline runs the apply using locked-down credentials, and logs everything centrally.
- Drift detection alerts you if someone later bypasses the process with a manual console change.
From an auditor’s perspective, this provides traceability, approvals, and tested controls. From an engineer’s perspective, it is “just” a pull request with good automation behind it. That is exactly the alignment you want.
Migrating From Ad-Hoc Infrastructure to IaC
Many fintechs already have a running product by the time they adopt IaC seriously. A big-bang rebuild is risky and often unnecessary. A more incremental approach works better.
A pragmatic path looks like this:
- Start with an inventory. Map out your current infrastructure: networks, data stores, workloads, CI/CD, observability, and third-party integrations.
- Design a target structure. Decide how you want to organise repositories, modules, and environments. Sketch out your landing zone, domain-oriented stacks, and shared modules.
- Import critical resources. Begin with networking, IAM, and core data stores. Use Terraform or OpenTofu to import existing resources so IaC can describe them without immediately changing behaviour.
- Introduce orchestrated workflows. Connect your IaC to CI/CD or onboard it into a platform to get consistent plans, policy checks, applies, and audit trails.
- Tighten the rules over time. Gradually move from “code plus console” to “code only, console in emergencies”. Enable drift detection so any out-of-band changes get caught and reconciled back into code.
Final Thoughts
For fintech companies, Infrastructure as Code is not just another DevOps trend. It is a way to reconcile three forces that usually pull in different directions: the need to ship fast, the need to stay secure, and the need to satisfy regulators and partners.
By moving infrastructure into code, you gain a clear, testable, and auditable model of your systems. Tools like Terraform and OpenTofu give you the language to express that model. Platforms like Spacelift or HCP help you turn it into governed workflows with policy as code, drift detection, and robust audit trails. But the most important change is cultural: infrastructure stops being an opaque, manually managed asset and becomes part of your product, developed with the same rigour as the application itself. That is exactly the kind of foundation you want when you are building software that moves money.








