Client sent us a repo… with a backdoor. Security in software development
Hi everyone!
This post is going to be a bit long, but it’s important because we encountered a SCAM with one of our recent leads, and I wanted to briefly share what we found, what raised red flags during our interactions with the potential client, and what takeaways we drew from the situation.
Long story short: We received a repo that had a backdoor likely designed to steal env variables or crypto keys.
Project: An online chess game with blockchain functionality. The client claimed the app was ~30% complete and that they needed blockchain integration. There was even a kind of whitepaper. At first glance, it looked like a legit project in need of further development. The budget was fine, everything looked potentially attractive. Our task was to review the client’s repo and present an offer.
We were given access to a monorepo consisting of the backend server with the game, API, and frontend. The repo at first glance looked like many other in-progress projects—nothing that particularly stood out. We did an initial analysis and prepared an offer.
So what actually happened during the meeting with the client that made us cut off talks and discover what we did?
The client didn’t speak English at all. The conversation was very difficult. No camera.
The client didn’t understand what we were asking. We asked for access to the smart contracts repo, and he shared the same monorepo again.
The client insisted we download the repo, run it, and go through tasks together. HUGE RED FLAG
The client didn’t talk about sales or collaboration, just pushed for us to run the code.
The repo had no commit history—uploaded just before the meeting. The commits were made by a newly created account with no contribution history.

What did we find during the later analysis of the repo?
In one of the routes, there was indeed obfuscated JS code acting as a backdoor. It was placed on the last line of a file, padded with hundreds of spaces so that a developer manually reading the code would likely overlook it. The final line was over 1,000 characters long. The code created a .js file in the .vscode folder, ran it, installed dependencies using npm i --silent, and launched a background script every 10 minutes. Due to obfuscation, full reverse engineering wasn’t possible.
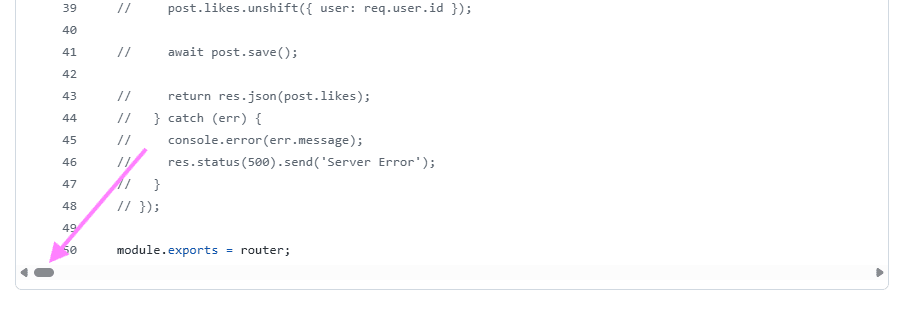
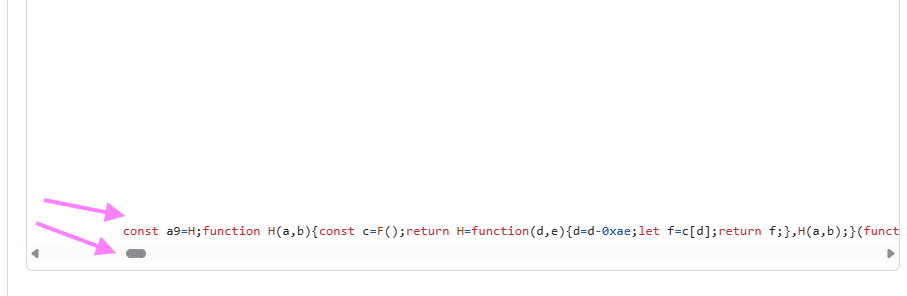
Where did we slip up?
Primarily in doing a visual repo check. Also, the first AI-assisted analysis didn’t flag anything because the prompt was focused on technical evaluation and project completion level.
What did we do right?
We didn’t run the code. Simply cloning the repo wasn’t dangerous. We cut off communication with the “client” at the right moment. We conducted a post-mortem analysis. We prepared a summary.
TAKEAWAYS?
During the sales phase, there’s no need to run foreign code
In general, you should never run code from unknown sources—this scam tactic is also used in fake job interview tasks.
If you absolutely must run unknown code, do it in a fully virtualized environment.
When doing AI-assisted code analysis, prompts should explicitly instruct AI to look for potentially malicious code.
In IDEs, auto-running scripts via AI tools should be disabled. (e.g., in the Cursor editor)
For the curious, here’s the reverse engineering OpenAI helped us with: https://chatgpt.com/s/dr_6819d873cbf48191a3d534054e655af2
Thanks for reading—let’s hope we all get as few leads like this as possible. 🙂







