MedTech IP Protection: Cloud vs Desktop Security Guide

A growing share of MedTech value lives in software algorithms. That makes your IP a target. You can best protect it by keeping the algorithm server-side in the cloud and using layered defenses only when an offline desktop is truly required. This article shows you when to choose cloud, when you must go offline, and exactly how to raise the cost of attacks.
Key Points
|
Why Is Desktop IP Protection Problematic?
Desktop software runs in environments you do not control. Even with obfuscation and licensing, a determined attacker can inspect, patch, or clone it. Your goal is not perfect safety; it is to make attacks uneconomical.
Offline constraints remove live checks. Users can roll back virtual machines, image disks, or change system clocks to bypass naive counters. Re‑installs erase state. Meanwhile, advanced tools can analyze binaries and memory during runtime. Hospitals may ask for offline continuity, but that shifts exposure from the server to user hardware. Accept that risk profile up front and plan defenses accordingly.
Use a Cloud-First Architecture To Best Protect IP
The simplest way to protect your algorithm is to never ship it. Keep it on the server and let the desktop app handle auth, file upload, job orchestration, and results.
In practice that means identity (for example, Amazon Cognito), encrypted transfer (TLS), direct uploads to object storage (presigned URLs to Amazon S3), server‑side analysis workers, and complete audit logs. You patch once and everyone gets the fix. Access is centralized. Infrastructure security and certifications from cloud providers support GDPR programs.
For context, innovation pressure is rising: AI‑based MedTech patent applications have surged since 2018, reaching 2,771 in 2022, with imaging and diagnostics leading, according to the Marks & Clerk 2023 AI report on MedTech patents.
To accelerate a secure cloud build, consider our custom healthcare software development services. We design cloud-first architectures that keep IP server-side while ensuring compliance with data protection requirements.
Design For GDPR Compliance Without Exposing IP
Healthcare data changes the calculus. You must protect patient privacy and prove it. Cloud and private/on‑prem cloud make it easier to centralize identity, isolate networks, and audit access. Use strong authentication, encrypt in transit, restrict access by role, log every touch, and set retention policies. For strict isolation or data residency, deploy into a VPC or private environment with no public endpoints.
When Offline Desktop Makes Sense
Default to cloud. Go offline only when connectivity, data‑location constraints, or clinical workflows make server‑side execution impractical. And accept higher IP exposure and delivery costs when you do.
Typical triggers include:
- Unreliable or prohibited connectivity at the point of care
- Strict data residency that forbids cloud transfer
- Time‑critical edge processing where network latency is unacceptable
- Air‑gapped environments that demand local operation
Before committing, validate that the offline benefit clearly outweighs the risk and operational overhead, and be ready to implement a defense‑in‑depth plan—outlined next.
How To Secure Offline Desktop Apps: A Defense-In-Depth Plan
Combine legal protections, technical hardening, and organizational controls to raise attacker cost and meet compliance.
If continuity or bandwidth constraints force offline operation, stack multiple controls. No single layer is enough, and some users will still bypass them. You are raising cost, not stopping attacks.
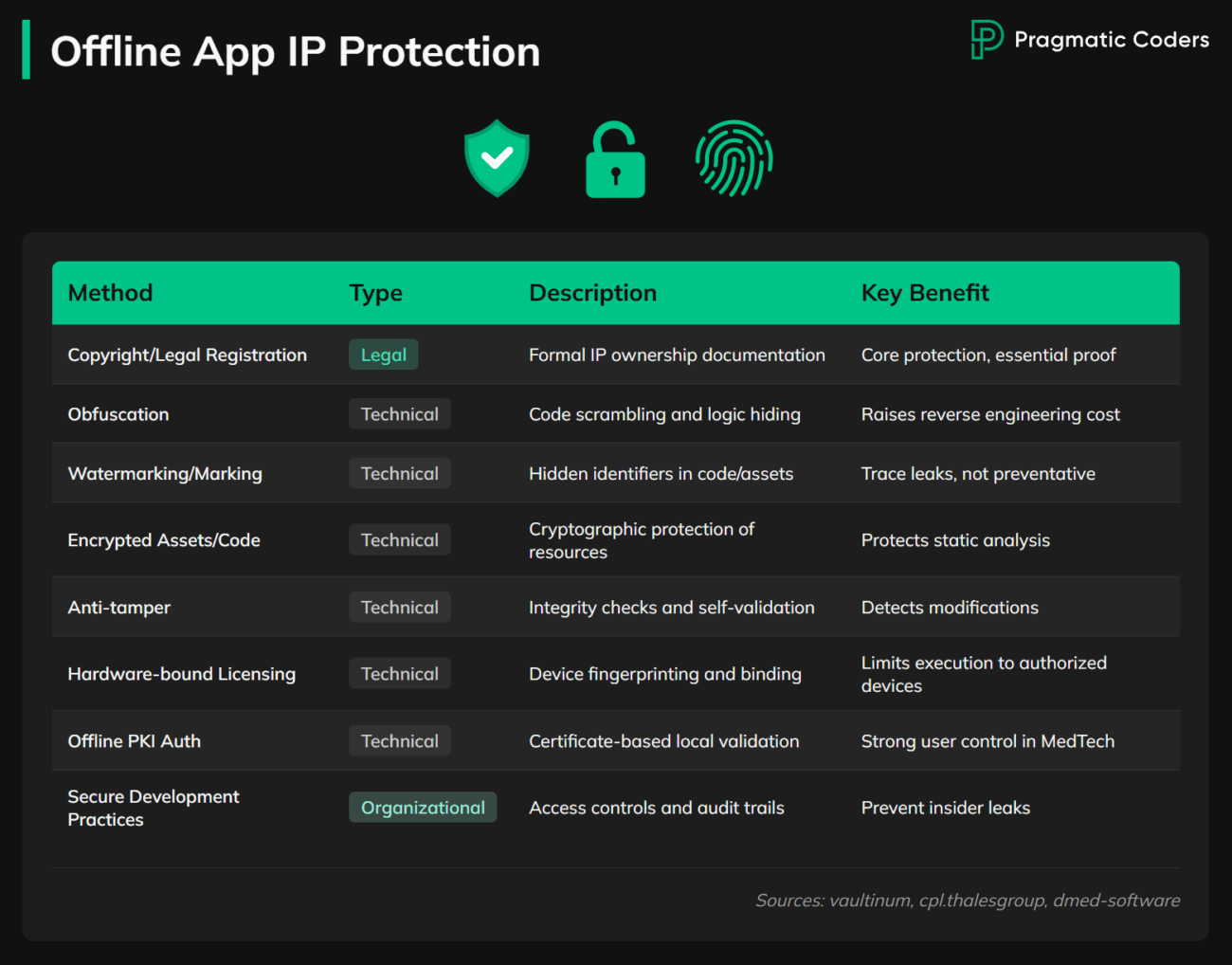
Legal Protections And Documentation
Lock down ownership early. Registrations and tight contracts give you leverage when code leaks.
- Register copyrights early and after significant updates to establish authorship.
- Use strong NDAs, explicit IP assignment for contractors, and clear employment IP clauses.
- Consider patents for novel methods and trademarks for brand protection where appropriate.
Technical Measures (Offline-Friendly)
Your goal is economics: make reverse engineering costly and fragile for attackers in practice. Layer checks so a single bypass still fails to produce a usable build.
- Obfuscate and minimize exposed logic. Use Python obfuscation and migrate core routines to compiled C via Cython, then package with PyInstaller.
- Bind licenses to hardware. Activate once online; derive device keys from hardware identifiers and store license state securely (Registry/Keychain).
- Encrypt license state. Keep counters and expiry encrypted with per‑device keys; update and validate frequently.
- Sign binaries and verify at start. Sign on Windows and macOS; block execution if signatures fail or binaries are tampered with.
- Add runtime self‑protection. Detect debuggers, suspicious processes, and known injection patterns; shut down or degrade safely.
- Protect secrets in memory. Encrypt sensitive operations, rotate keys, and zero memory after use.
- Watermark builds. Embed invisible, traceable markers in binaries to attribute leaked copies.
- Encrypt sensitive code/assets. Decrypt in memory only and minimize the decrypted window.
- Add anti‑tamper integrity checks (self‑hashing/checksums) and fail safely on detection.
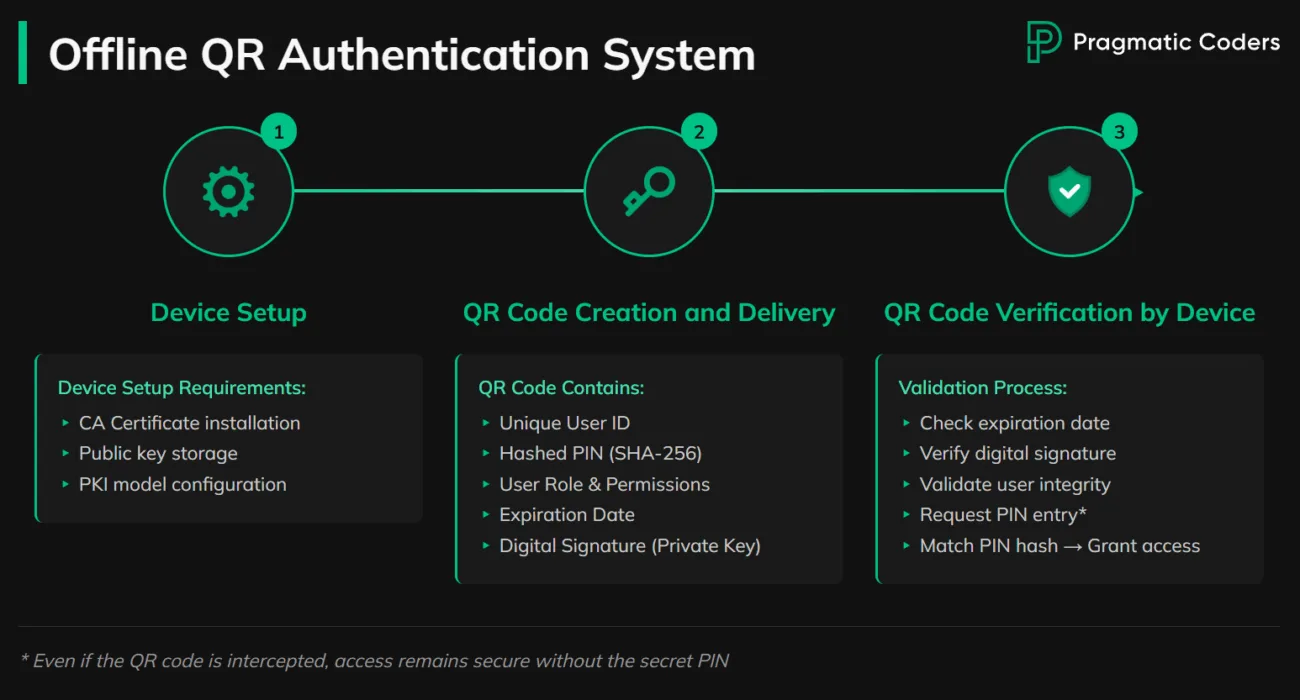
- Enable offline authentication for sensitive actions (e.g., PKI/QR‑code certificate challenges).
Threat Model: How Desktop Apps Get Broken (and What To Do)
Assume capable adversaries with time and tooling. Plan mitigations per vector and validate them in tests.
System‑level attacks include VM snapshots and disk images that preserve a “fresh” license. Binary‑level attacks include DLL hijacking or injection and direct patching of license checks. Reverse engineering combines static disassembly with dynamic runtime analysis and memory scanning to extract secrets or bypass flows. Counter these with signature self‑checks, scattered and redundant license validations, debugger/VM detection, and encryption for sensitive material in memory.
Practical Organizational Security
Controls crumble where process is loose. Secure the pipeline and physical access so protections hold in the real world.
- Secure the development pipeline: encrypted repos, MFA, least‑privilege access, and monitored CI/CD.
- Physically secure build and distribution systems, especially in regulated environments.
MedTech‑Specific Considerations
Regulation sets the floor, not the ceiling in MedTech. Map controls to recognized standards and keep traceability even fully offline.
- Align controls with standards (ISO 27001, SOC 2) and, when handling PHI, HIPAA/HITRUST.
- Maintain tamper‑resistant offline audit logs for critical operations and access attempts.
Implement Licensing And Business Controls That Deter Abuse
Licensing is about economics. On the cloud, authorize people, not machines. Check entitlements server‑side and manage access via subscription. Offline, bind licenses to devices and encrypt entitlement state; plan renewal and revocation paths. Expect re‑installs, time skew, and VM rollbacks. Rate‑limit sensitive flows and keep randomness high where it matters.
Choose Your Reference Architecture And Data Flow
Choose an approach that keeps the algorithm server‑side and matches your workloads; serverless simplifies spiky CPU work, while containers suit long‑running/GPU jobs and on‑prem needs.
Below are two proven patterns our teams use; pick based on runtime, compliance, and operational constraints.
Serverless Pattern: Lambda + S3 + Step Functions
Pick serverless when workloads are spiky and you want minimal ops with rapid iteration. Use Electron + React on desktop for UX and file handling. Authenticate (e.g., Amazon Cognito) and call APIs through API Gateway. Upload data via presigned URLs to Amazon S3. Orchestrate analysis with AWS Step Functions and invoke Node.js/TypeScript workers on AWS Lambda; persist results and audit logs. Serve the admin app (React) from S3/CloudFront for usage, licensing, and monitoring. Benefits: minimal ops, scale-to-zero, fast iteration; trade‑offs: limited for long‑running or GPU workloads.
Containerized Pattern: Microservices On EKS/ECS
Choose containers for long‑running or GPU workloads and for on‑prem/private deployments where you need full runtime control. Keep the same desktop and admin apps, but run backend services as containers. Expose APIs via an Application Load Balancer; handle auth/licensing as separate services; push jobs to a queue (SQS/Kafka); execute analysis as Kubernetes Jobs (EKS) or ECS tasks, including GPU nodes when needed; store data in S3 or on‑prem S3‑compatible storage (e.g., MinIO) for data residency. Benefits: full runtime control, supports long‑running/GPU workloads, portable to private/on‑prem; trade‑offs: higher operational overhead and cluster hardening requirements.
Balance Cost, UX, And Delivery
Cloud gives you stronger IP protection and faster iteration. Desktop gives you immediate local analysis and offline continuity. Cloud removes the pain of redistributing binaries for every fix, while desktop increases delivery effort for each update. If you add private (self-hosted) AI/LLM features, expect non‑trivial monthly costs even on CPU‑only instances and slower responses compared to vendor APIs; keep that in mind when choosing where the algorithm lives.
Choose Cloud, On‑Prem, Or Offline With This Framework
Pick cloud by default. Move to private/on‑prem when regulators or data residency force it. Accept offline desktop only when you cannot rely on connectivity and you have a plan to layer defenses.
- Cloud: continuous internet, high IP value, need for rapid updates, strong audit needs.
- Private/On‑Prem: strict isolation, internal networks, regulatory constraints on external services.
- Offline Desktop: continuity must be guaranteed without internet or bandwidth makes uploads infeasible; implement the defense‑in‑depth pattern above.
Conclusion
Keep your MedTech algorithm on the server when you can; that is how you best protect your IP and move fast. When offline is mandatory, treat security as an economic game. Stack protections, sign and verify, encrypt state and memory, and monitor at runtime to raise the attacker’s cost. If you want a tailored blueprint, Pragmatic Coders can help you design the right cloud, on‑prem, or offline architecture and deliver it safely.